When purchasing a new Windows computer from a manufacturer, mainly Dell – we have noticed that they like to install different language versions of Microsoft 365, and Microsoft OneNote.
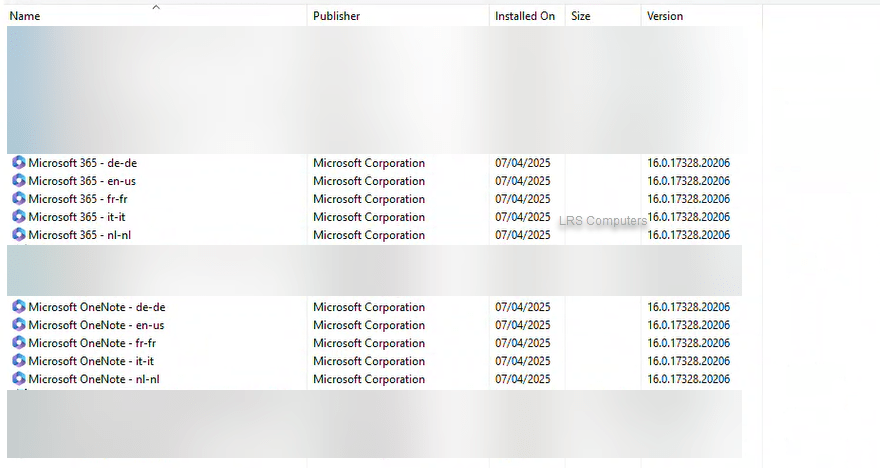
The above can be totally fine, but as premade computers from a manufacturer – they are often packed with bloatware and unnecessary applications.
As I mainly deal with computers for businesses and clients who have their Microsoft 365 subscription, we much prefer to uninstall the above and install a fresh copy of Microsoft 365 (Office) directly from their account / subscription.
We can uninstall directly from Control Panel, but each one can take 2-3 minutes.
In this post, I will show you how I uninstall all the above with a few clicks.
Read More »